Secure email: Encrypt and sign your emails with PGP/GnuPG
Email is fundamentally insecure. There are such a plethora of issues with it, it is crazy to think about the kind of information sent with it. It is probably even crazier when you realize we’ve had a solution for sending secure email since 1991.
Fundamental issues with email
There’s lots of fundamental issues with email. Here are some of them:
1. Email travels and is stored in plain text
This means that anyone managing a server or network device along the way can read (and modify) the email as they like. You may compare it to sending a postcard by regular mail. Any information in it should be regarded as publicly available. Ever heard of “leaked emails”? Yeah. It doesn’t take much of a hacker to do that.
2. There are no integrity checks
When you send an email, you don’t know whether it will end up at the recipient without modification. The recipient can’t trust the content, as they can’t be assured it haven’t been modified along the way. This happens much more than you think. Usually “just” some tracking code or ads are inserted.
3. There is no sender verification
Ever heard of phishing? Do you know how to impose as someone? Go into your email client and change the email address. Now you can send emails on behalf of that person. Usually, there is no way to detect if an email was really sent by someone or not.
Pretty Good Privacy (PGP)
Now, go more than two and a half decades back, to 1991. Phil Zimmermann is very much aware of these issues with email and invents a solution he calls Pretty Good Privacy, or PGP for short. PGP provides cryptographic privacy and authentication for just about any data.
PGP is used for signing, encrypting, and decrypting texts, e-mails, files, directories, and whole disk partitions and to increase the security of e-mail communications.
It works like this:
Cryptographic key pair
You create a cryptographic key pair. This pair consists of a private and a public key. The private key must be kept really, really secret and secure. The public key should be made as publicly available as possible: Uploaded to special key servers and posted on your blog and social media profiles.
Encrypted content
When someone wants to send you an email, they encrypt it with your public key. Only the secret key can be used to decrypt the contents. This means that only you can read the content.
Digital signature
Also, whether you choose to encrypt the content or not, you can digitally sign the email message you’re sending. Then you use your private key to generate and attach a signature based on the content of the email message. The recipient can then use your public key to verify that the signature was really made with your private key – thus really signed by you. This verifies both the sender and the content. If the signature doesn’t match with both the sender and the content, something phishy is going on.
Pretty good, but not full privacy
Encryption and signing solve all three issues I mentioned at the beginning. However, PGP doesn’t provide full privacy: Headers are still public. This includes info on who sent it, when they sent it, and possibly where did they send it from.
OpenPGP and GnuPG are free
Since 1997 there has been an open standard for PGP encryption called OpenPGP. This is the standard everybody is using today, and you don’t really have to worry about any incompatibilities at all.
GNU Privacy Guard (GnuPG or GPG) is a free software implementation of OpenPGP and is interoperable and compatible with other OpenPGP-compliant software.
In general, the terms GnuPG, GPG, GNU Privacy Guard, OpenPGP and PGP are used interchangeably. Technically, OpenPGP (Pretty Good Privacy) is the encryption standard, and GNU Privacy Guard (often shortened to GPG or GnuPG) is the program that implements the standard.
– Free Software Foundation
Why doesn’t everybody use secure email?
I don’t know. Maybe too difficult to get started with? Concept to advanced too understand? Not reached critical mass? Beats me. It’s not really difficult to get started, and when you are up and running, it is really easy to use.
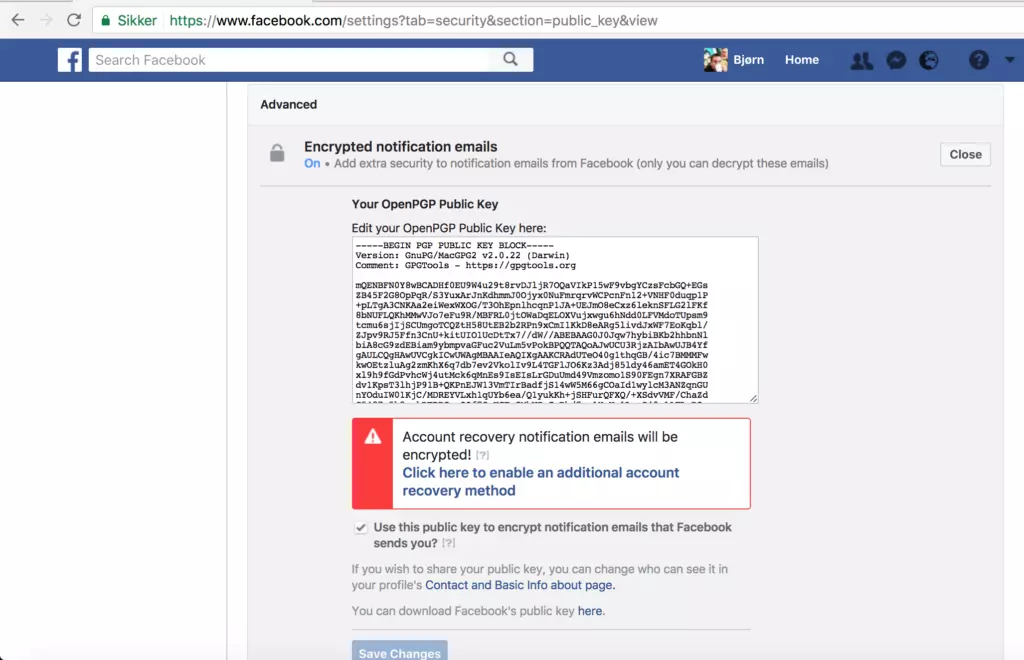
With all kinds of email scandals, spear phishing attacks and corporate and governmental surveillance schemes, there seems to me that secure email has gotten more popular the last few years. More and more people and services are using it. Even Facebook will send you all emails encrypted and signed if you enter your public key in your profile settings. No more Facebook account phishing attacks for you!
How to get started with secure email
The Free Software Foundation has published an excellent step-by-step tutorial that guides you through the steps, explaining everything nicely along the way. Just select if you use GNU/Linux, MacOS or Window at the top. You’ll find the guide “Email Self Defence” here.
Send me a secure email message
If you want to send me an email, my fingerprint is:
5029 E0D0 F458 72E4 09D3 308D 1D51 378E E348 35B6
My full OpenPGP (GnuPG) public key is also available here.
Good luck, have fun and stay safe!
4 thoughts on “Secure email: Encrypt and sign your emails with PGP/GnuPG”
See original article here.
The Tutorial below shows how to setup your Email Encryption with Mozilla Thunderbird. OpenPGP is now integrated on Thunderbird, so the Enigmail extension is not required anymore.
Or install the Mailvelope extension on your browser and use it on your webmail. Although Mailvelope being an extension for most of the current browsers has less features / options than Thunderbird. It encrypts your message and inserts it into your webmail on Gmail and possibly a few other email providers as well.
Also have noticed that Encrypted email sent with Thunderbird can't be decrypted with Mailvelope. Whereas Encrypted email sent with Mailvelope can be decrypted with Thunderbird. (this may not be the case anymore.) Also if you export your secret/private key to OpenKeyChain and setup your email on K9 Mail (and maybe R2Mail2) K9 Mail should be able to decrypt the emails sent with Thunderbird and Mailvelope, if you're wondering about being able to read your email on both mobile and stationary devices(computers).
If you have Microsoft Outlook and don't wish to switch to Thunderbird, please directly install GPG4WIN. Also use this guide to setup the email encryption on Outlook. It's a longer process on Outlook though, while still possible.
On your Android phone install K-9 Mail or R2Mail2 & OpenKeyChain. Create your key pairs on Thunderbird and then export your secret/private key to OpenKeychain. (Because exporting secret/private keys on OpenKeyChain creates PGP encrypted files with a long number which will have to be entered to decrypt on your computer. You'll need GPG4WIN, or an equivalent for Mac/IOS.) (R2Mail2 is not free)
On Mac you can install GPG Tools, and on IOS you could try PGP Everywhere.
Also recommend Password Safe, a simple Password Manager application for Windows designed by renowned security technologist Bruce Schneier with clones for Android & Mac/IOS, and RoboForm or Dashlane or LastPass. Password Safe is an OpenSource software that runs on your computer/phone and Dashlane & LastPass are online Password Manager accounts with browser extensions so they need a strong password for the Master Password, whereas Password Safe does not, unless you share use of a computer with others. (RoboForm is software that runs on a computer, and comes with extensions for most web browsers.)
Email Self-Defense
- English - v4.0
- čeština - v4.0
- Deutsch - v4.0
- ελληνικά - v3.0
- español - v4.0
- فارسی - v4.0
- français - v4.0
- italiano - v3.0
- 日本語 - v4.0
- português do Brasil - v3.0
- română - v3.0
- русский - v4.0
- Shqip - v4.0
- svenska - v4.0
- Türkçe - v4.0
- 简体中文 - v4.0
- Translate!
We fight for computer users' rights, and promote the development of free (as in freedom) software. Resisting bulk surveillance is very important to us.
Please donate to support Email Self-Defense. We need to keep improving it, and making more materials, for the benefit of people around the world taking the first step towards protecting their privacy.
 Bulk surveillance violates our fundamental rights and makes free speech
risky. This guide will teach you a basic surveillance self-defense skill: email
encryption. Once you've finished, you'll be able to send and receive emails
that are scrambled to make sure a surveillance agent or thief intercepting
your email can't read them. All you need is a computer with an Internet
connection, an email account, and about forty minutes.
Bulk surveillance violates our fundamental rights and makes free speech
risky. This guide will teach you a basic surveillance self-defense skill: email
encryption. Once you've finished, you'll be able to send and receive emails
that are scrambled to make sure a surveillance agent or thief intercepting
your email can't read them. All you need is a computer with an Internet
connection, an email account, and about forty minutes.
Even if you have nothing to hide, using encryption helps protect the privacy of people you communicate with, and makes life difficult for bulk surveillance systems. If you do have something important to hide, you're in good company; these are the same tools that whistleblowers use to protect their identities while shining light on human rights abuses, corruption and other crimes.
In addition to using encryption, standing up to surveillance requires fighting politically for a reduction in the amount of data collected on us, but the essential first step is to protect yourself and make surveillance of your communication as difficult as possible. This guide helps you do that. It is designed for beginners, but if you already know the basics of GnuPG or are an experienced free software user, you'll enjoy the advanced tips and the guide to teaching your friends.
#1 Get the pieces
This guide relies on software which is freely licensed; it's completely transparent and anyone can copy it or make their own version. This makes it safer from surveillance than proprietary software (like Windows). Learn more about free software at fsf.org.
Most GNU/Linux operating systems come with GnuPG installed on them, so you don't have to download it. Before configuring GnuPG though, you'll need the IceDove desktop email program installed on your computer. Most GNU/Linux distributions have IceDove installed already, though it may be under the alternate name "Thunderbird." Email programs are another way to access the same email accounts you can access in a browser (like Gmail), but provide extra features.
If you already have an email program, you can skip to Step 1.b.
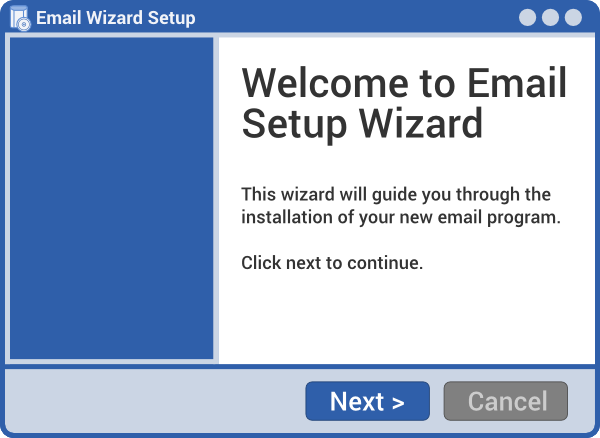
Step 1.a Set up your email program with your email account
Open your email program and follow the wizard (step-by-step walkthrough) that sets it up with your email account.
Look for the letters SSL, TLS, or STARTTLS to the right of the servers when you're setting up your account. If you don't see them, you will still be able to use encryption, but this means that the people running your email system are running behind the industry standard in protecting your security and privacy. We recommend that you send them a friendly email asking them to enable SSL, TLS, or STARTTLS for your email server. They will know what you're talking about, so it's worth making the request even if you aren't an expert on these security systems.
Troubleshooting
- The wizard doesn't launch
- You can launch the wizard yourself, but the menu option for doing so is named differently in each email program. The button to launch it will be in the program's main menu, under "New" or something similar, titled something like "Add account" or "New/Existing email account."
- The wizard can't find my account or isn't downloading my mail
- Before searching the Web, we recommend you start by asking other people who use your email system, to figure out the correct settings.
- Don't see a solution to your problem?
- Please let us know on the feedback page.
Step 1.b Install the Enigmail plugin for your email program
In your email program's menu, select Add-ons (it may be in the Tools section). Make sure Extensions is selected on the left. Do you see Enigmail? Make sure it's the latest version. If so, skip this step.
If not, search "Enigmail" with the search bar in the upper right. You can take it from here. Restart your email program when you're done.
There are major security flaws in versions of GnuPG prior to 2.2.8, and Enigmail prior to 2.0.7. Make sure you have GnuPG 2.2.8 and Enigmail 2.0.7, or later versions.
Troubleshooting
- I can't find the menu.
- In many new email programs, the main menu is represented by an image of three stacked horizontal bars.
- My email looks weird
- Enigmail doesn't tend to play nice with HTML, which is used to format emails, so it may disable your HTML formatting automatically. To send an HTML-formatted email without encryption or a signature, hold down the Shift key when you select compose. You can then write an email as if Enigmail wasn't there.
- Don't see a solution to your problem?
- Please let us know on the feedback page.



![[GNU Social]](http://static.fsf.org/nosvn/enc-dev0/img/gnu-social.png)
![[Mastodon]](http://static.fsf.org/nosvn/enc-dev0/img/mastodon.png)
![[Reddit]](http://static.fsf.org/nosvn/enc-dev0/img/reddit-alien.png)
![[Hacker News]](http://static.fsf.org/nosvn/enc-dev0/img/hacker-news.png)










I’ve tried using PGP in the past, but always give up on it after a month or two. I use too many different devices and keeping the keys in sync is a chore I’d rather avoid. Every single time I’ve used it over the years, any email I receive that use PGP have to wait days longer than other email before I get around to a client that is configured to use it.
I believe the main problem people have with PGP is that sooner or later they’ll loose their keychain, get frustrated that they can’t recover it, and never touch PGP again. The market move away from email clients to ad-funded webmail probably didn’t help either.
I’d go so far as to say that I’m motivated to use PGP, yet even I find it too cumbersome to actually use it.
For anyone interested in adopting PGP, then you should check out the Free Software Foundation’s Email Self Defense site.
Maybe the issue then is that you use it too seldom? If you had the need to use it on a daily basis, and a large enough share of your important email was encrypted, you would perhaps have the motivation to setup your all your infrastructure/clients to use PGP?
Possibly. However, when something is this difficult to use then no one will actually use it (including its inventor, who uses iOS.) I’m guessing that 90% of emails I’ve sent with PGP have gotten a reply saying the keys are lost or that the recipient otherwise can’t decrypt the message for some other reason. —attaching signatures to messages also creates a lot of confusion for non-PGP users who wastes their own and my time asking what the signature is all about.
Mailpile was the webmail encryption crowdfunding star of 2013, but the project has yet to release a single stable version. They’re getting close, but their technology choices have already made it outdated before their first release.
There are very few good email clients on the market now, and very fewer that support PGP. Even on Linux, there is only a handful of actively maintained email clients – and the most popular once either don’t support PGP at all or require the user to install weak dependencies or plugins.
S/MIME on the other hand has better client support (including Outlook, iOS Mail, and the stock Mail app on Android) and a better user experience. The only problem? You have to pay a public certificate authority to issue your certificate on a yearly basis.
You can get free certificates for S/MIME for personal/non-commercial use from Comodo: https://comodo.com/home/email-security/free-email-certificate.php
You’ll still have to get a new one on a yearly basis, though. Otherwise, it works fine, yes.